Introduction
This tutorial will teach you how to set up your own robust email server. We are focusing on a small personal server with up to a few email accounts. After following this guide, you will have a fully functional mail server and you can connect with your favourite client to access, read and send emails. The Anti-Spam configuration will drop unwanted messages.
This tutorial will use yourdomain.com as domain name and mail.yourdomain.com as hostname for our mail server. The desired email address will be yourname@yourdomain.com. We assume that our server has the IP address 1.2.3.4.
Software and technologies used
- Postfix v2.9.6 as SMTP server
- Dovecot v2.0.19 as IMAP server
- We will use Unix user accounts and tunnel the SASL authentication through TLS
- Emails in transit (inbound/outbound) will be encrypted using TLS if supported by the foreign mail server
- Postgrey v1.34 – to reject spam from the beginning (more about postgrey)
- SPF (Sender Policy Framework) validating to reduce spam (more aboutSPF)
- SPF and DMARC DNS entry to prevent spoofing
- DKIM (Domain Keys Identified Mail) to sign our email messages (moreabout DKIM)
Prerequisites
Personal
Every step will be explained in the tutorial and you will get it running even with minimal Unix knowledge. Nevertheless, you should be used to work on the command-line and know how to use a text editor. Furthermore it takes some Unix skills to administrate the working mail server.
You’re invited to follow the links in this tutorial to learn more about the software and techniques used.
System
- A VPS running Ubuntu 12.04 or 14.04 (setup will be similar on any Debian based distribution). (Get a VPS here)
- Your own FQDN domain name.
We will be working on a root shell and the tutorial will use vim as text editor.
Preparing our system
Setting up the host name
echo mail.yourdomain.com > /etc/hostname
Adding our domain to /etc/hosts
vim /etc/hosts
We add yourdomain.com and mail.yourdomain.com in the first line.
127.0.0.1 localhost yourdomain.com mail.yourdomain.com
Setting up the mailname
echo yourdomain.com > /etc/mailname
That’s the name that will appear on the right side of the ‘@’ in our email address. In this case, yourdomain.com.
Installing required packages
Updating the system
apt-get update && apt-get upgrade
Installing
apt-get install postfix postfix-policyd-spf-perl postgrey dovecot-core dovecot-imapd opendkim opendkim-tools && postfix stop
Hit ‘No’ if asked to create a SSL certificate. Choose Internet Site and press ‘ok’ 2 times when asked by the postfix installer.
Setting up DNS
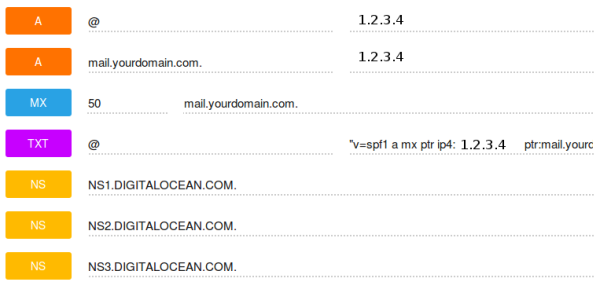
We assume that our domain is already setup in the DNS control panel and we see the default DNS records.

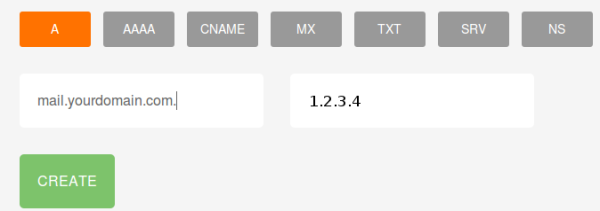
Setting up the A record
(There is a ‘dot’ after the domain name)
Setting up the MX record
(There is a ‘dot’ after the domain name)
Setting up the SPF record
We create a new TXT record
"v=spf1 a mx ip4:1.2.3.4 -all"
The SPF record protects from email spoofing. It will simply tell other mail servers that only our server is authorized to send emails for yourdomain.com (more aboutSPF).
Setting up the DMARC record
We create a new TXT record named _dmarc.yourdomain.com.
(There is a ‘dot’ after the domain name)
"v=DMARC1; p=quarantine; rua=mailto:postmaster@yourdomain.com"
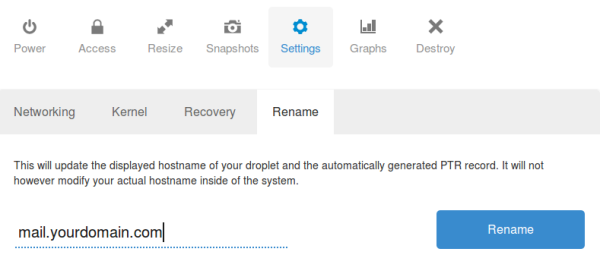
Now we will setup the hostname for the PTR record
Our configuration should look similar to this
It will take a while to propagate the new configuration throughout the entire internet.
Generating SSL certificates
There are different ways to generate a SSL certificate. The tutorial will use a self signed certificate but we could also use a CAcert, which can be obtained for free from startssl.
Either ways, the connection from our email client to the mail server will be encrypted.
Creating the certificate
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/mail.yourdomain.key -out /etc/ssl/certs/mail.yourdomain.pem
We will be asked to answer a few questions. It is important that we enter mail.yourdomain.com as Common name.
Generating a 2048 bit RSA private key
..........+++
..................................................................+++
writing new private key to '/etc/ssl/private/mail.yourdomain.key'
- -----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
- -----
Country Name (2 letter code) [AU]:AT
State or Province Name (full name) [Some-State]:Styria
Locality Name (eg, city) []:Vienna
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:mail.yourdomain.com
Email Address []:postmaster@yourdomain.com
Postfix Configuration
Backing up the configuration files
cp /etc/postfix/master.cf /etc/postfix/master.cf_orig &&
cp /etc/postfix/main.cf /etc/postfix/main.cf_orig
Configuration in main.cf
vim /etc/postfix/main.cf
We empty the file and add our configuration
#Base config
myhostname = mail.yourdomain.com
myorigin = /etc/mailname
mydestination = $myhostname, $mydomain, localhost, localhost.$mydomain
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
relay_domains = $mydestination
syslog_name=postfix/submission
#Aliases / Recipients
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
local_recipient_maps = proxy:unix:passwd.byname $alias_maps
#SSL/TLS
smtpd_tls_cert_file=/etc/ssl/certs/mail.yourdomain.pem
smtpd_tls_key_file=/etc/ssl/private/mail.yourdomain.key
smtpd_use_tls=yes
smtpd_tls_auth_only = yes
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
smtpd_tls_security_level=may
smtp_tls_security_level=may
smtpd_tls_protocols = !SSLv2, !SSLv3
smtpd_tls_wrappermode=no
smtpd_sasl_type=dovecot
smtpd_sasl_path=private/auth
smtpd_sasl_auth_enable=yes
milter_macro_daemon_name=ORIGINATING
#Security and Anti-Spam cinfig
policy-spf_time_limit = 3600s
smtpd_helo_required = yes
smtpd_recipient_restrictions =
reject_non_fqdn_recipient
reject_unknown_recipient_domain
permit_mynetworks
permit_sasl_authenticated
reject_unauth_destination
check_policy_service unix:private/policy-spf
check_policy_service inet:127.0.0.1:10023
smtpd_helo_restrictions =
permit_mynetworks
reject_non_fqdn_helo_hostname
reject_invalid_helo_hostname
smtpd_client_restrictions=
permit_mynetworks
permit_sasl_authenticated
reject_unknown_client_hostname
smtpd_data_restrictions =
reject_unauth_pipelining
#DKIM
milter_default_action = accept
milter_protocol = 6
smtpd_milters = inet:localhost:8891
non_smtpd_milters = inet:localhost:8891
Configuration in master.cf
vim /etc/postfix/master.cf
This line must be active:
smtp inet n - - - - smtpd
We uncomment the following:
submission inet n - - - - smtpd
and add those 2 lines at the end of the file (there are 2 whitespaces
before the second line).
policy-spf unix - n n - - spawn
user=nobody argv=/usr/sbin/postfix-policyd-spf-perl
More information about the postfix configuration parameters can be found here.
Dovecot Configuration
Backing up the configuration file
cp /etc/dovecot/dovecot.conf /etc/dovecot/dovecot.conf_orig
Configuration in dovecot.conf
vim /etc/dovecot/dovecot.conf
We empty the file and add our configuration.
disable_plaintext_auth = no
mail_privileged_group = mail
mail_location = mbox:~/mail:INBOX=/var/mail/%u
userdb {
driver = passwd
}
passdb {
args = %s
driver = pam
}
protocols = " imap"
protocol imap {
mail_plugins = " autocreate"
}
plugin {
autocreate = Trash
autocreate2 = Sent
autosubscribe = Trash
autosubscribe2 = Sent
}
service auth {
unix_listener /var/spool/postfix/private/auth {
group = postfix
mode = 0660
user = postfix
}
}
ssl=required
ssl_cert = /etc/ssl/certs/mail.yourdomain.pem
ssl_key = /etc/ssl/private/mail.yourdomain.key
More information about the dovecot configuration parameters can be found here.
Restarting dovecot
service dovecot restart
Adding our mail user
Now we add the user for our mail account. In this example our email
address will be yourname@yourdomain.com.
We can add as many users/email addresses as we want.
adduser --gecos '' --shell /bin/false yourname
Setting Aliases
vim /etc/aliases
The configuration can be adapted to your needs.
Here we tell postfix to forward all messages addressed to aliases to the mailbox of user: yourname.
mailer-daemon: postmaster
postmaster: root
nobody: root
hostmaster: root
usenet: root
news: root
webmaster: root
www: root
ftp: root
abuse: root
noc: root
security: root
admin: root
root: yourname
Compiling the alias file
newaliases
Setting up DKIM (Domain Keys Identified Mail)
Creating the directory and files
mkdir /etc/opendkim
vim /etc/opendkim/KeyTable
We enter the following line (all in the first line):
default._domainkey.mail.yourdomain.com mail.yourdomain.com:default:/etc/opendkim/default.private
vim /etc/opendkim/SigningTable
We enter the following line:
*@yourdomain.com default._domainkey.mail.yourdomain.com
Generating the key pair
opendkim-genkey -s default -d mail.yourdomain.com -D /etc/opendkim
Changing ownership of the private key file
chown opendkim:opendkim /etc/opendkim/default.private
Configuration in opendkim
vim /etc/default/opendkim
We add the line below to the configuration
SOCKET="inet:8891@localhost"
Configuration in opendkim.conf
vim /etc/opendkim.conf
We fill the file with our configuration
Syslog yes
SyslogSuccess Yes
LogWhy yes
UMask 002
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
Selector default
X-Header no
SignatureAlgorithm rsa-sha256
Canonicalization relaxed/simple
Mode sv
AutoRestart Yes
AutoRestartRate 5/1h
InternalHosts 127.0.0.1, localhost, yourdomain.com, mail.yourdomain.com
OversignHeaders From
Setting the DKIM DNS record
cat /etc/opendkim/default.txt
This is our public key which will be used to verify the signature in our emails.
default._domainkey IN TXT "v=DKIM1; k=rsa;
p=MIGfHL0GCSqGSIb3DQESYJFOA4GNADCBiQKBgQDS+vPyWRs7w32xomf2oZIexmS2TuQAXKPiQ3AXn4j25NOReXdgKxIqAwl3O7dQtgluWw+TH85Mrbmx5UgwaaLenj9cfe2IRvx7hvkj7+6i0XQqrWqZlMw+QAJxAGhfa/GVTYa+/7PFWfXLoqoBW5arE+wO20O2uw5Ik62HjkKZbQIDAQAB" ; ----- DKIM key default for mail.yourdomain.com
Now we add a new TXT record:
As ‘name’ we put (there is a ‘dot’ at the end):
default._domainkey.mail.yourdomain.com.
As ‘text’ we add (use your public key from /etc/opendkim/default.txt):
"v=DKIM1; k=rsa; p=MIGfHL0GCSqGSIb3DQESYJFOA4GNADCBiQKBgQDS+vPyWRs7w32xomf2oZIexmS2TuQAXKPiQ3AXn4j25NOReXdgKxIqAwl3O7dQtgluWw+TH85Mrbmx5UgwaaLenj9cfe2IRvx7hvkj7+6i0XQqrWqZlMw+QAJxAGhfa/GVTYa+/7PFWfXLoqoBW5arE+wO20O2uw5Ik62HjkKZbQIDAQAB"
It will take a while to propagate the new configuration throughout the entire internet.
Starting postfix and restarting opendkim
postfix start && service opendkim restart
Connecting with a Client
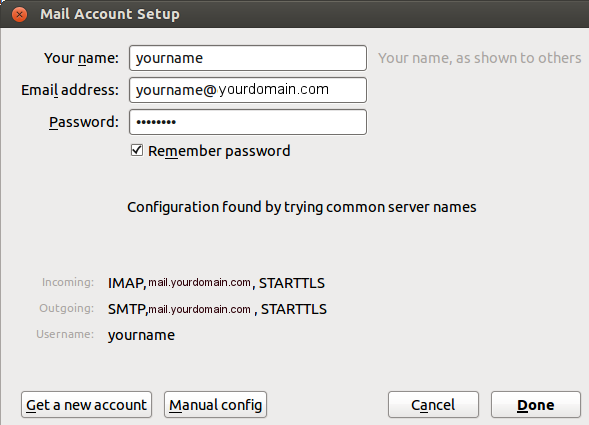
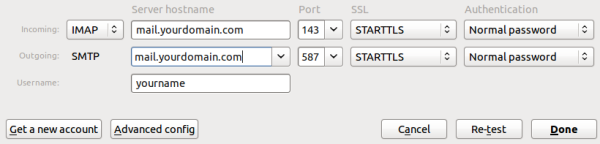
Now we will connect with our email client. In the tutorial we use Thunderbird as client.
Just add a new email account in Thunderbird and it will auto-detect the servers configuration.
The configuration should look like this:
Testing the mail server
It’s time to test our server. Let’s send and receive emails within Thunderbird.
We can observe the ongoing transactions and spot possible errors by monitoring our syslog.
tail -f /var/log/syslog
We can test our SPF and DKIM configuration here and DMARC here.
Some more testing can be done here, or here.
Postgrey in action
Pass:
May 11 16:26:38 mail postgrey[21408]: action=pass, reason=triplet found,delay=1290, client_name=another.server.com, client_address=4.2.3.1,
sender=user@another.server.com, recipient=yourname@yourdomain.com
Reject at first try:
May 10 12:42:33 mail postgrey[21408]: action=greylist, reason=new,
client_name=ns1.qubic.net, client_address=208.69.177.116,
sender=daemon@dk.elandsys.com, recipient=yourname@yourdomain.com 10
12:42:33 mail postfix/submission/smtpd[24718]: NOQUEUE: reject: RCPT
from ns1.qubic.net[208.69.177.116]: 450 4.2.0 yourname@yourdomain.com
: Recipient address rejected: Greylisted, see http://postgrey.schweikert.ch/help/yourdomain.com.html;
from=daemon@dk.elandsys.com to= yourname@yourdomain.com proto=ESMTP helo=
DKIM in action
Sending an email:
May 12 06:25:12 mail opendkim[1508]: 423AA62DC2: DKIM-Signature header
added (s=default, d=mail.yourdomain.com)
SPF in action
Pass:
May 10 14:28:47 mail postfix/policy-spf[1085]: Policy action=PREPEND
Received-SPF: pass (verifier.port25.com: 96.244.219.19 is authorized to
use 'auth-results@verifier.port25.com' in 'mfrom' identity (mechanism
'a' matched)) receiver=yourdomain.com; identity=mailfrom;
envelope-from="auth-results@verifier.port25.com";
helo=verifier.port25.com; client-ip=96.244.219.19
Reject:
May 12 16:15:25 mail postfix/policy-spf[20469]: Policy action=550 Please see http://www.openspf.net/Why?s=mfrom;id=someone 4yourdomain.com;ip=184.72.226.23;r=yourdomain.com
May 12 16:15:25 mail postfix/submission/smtpd[20463]: NOQUEUE: reject:
RCPT from node-mec2.wormly.com[184.72.226.23]: 550 5.7.1 yourname@ yourdomain.com : Recipient address rejected: Please see http://www.openspf.net/Why?s=mfrom;id=someone%
yourdomain.com;ip=184.72.226.23;r=yourdomain.com;
from=someone@yourdomain.com to=yourname@yourdomain.com proto=ESMTP
helo=
Congratulations
You did it! You setup our own mail server and do not depend anymore on
any email provider.
Our anti-spam setup should filter out 99% of all unwanted messages and
won’t drop a legitimate email. On the other hand, messages from our
server should not be declared as spam as it has a valid SPF record and
we are signing our messages.
Still getting a few spam messages and not tired yet? Go on over here.
Useful for troubleshooting
Verify DNS
Check reverse entry
dig -x 1.2.3.4 +short
Check MX record
dig yourdomain.com MX +short
Verify if ports are listening
netstat -tulpen|grep LISTEN
Enable verbose logging for postfix in /etc/postfix/master.cf
Just add the v at the end of the smtp line.
smtp inet n - - - - smtpd -v
Check the syslog with
tail -f /var/log/syslog
and observe the logging.
![c7Apht1[1]](https://skrilnetz.net/wp-content/uploads/2014/06/c7Apht11-600x171.png)
![cyFoSjh[1]](https://skrilnetz.net/wp-content/uploads/2014/06/cyFoSjh11-600x133.png)
Awesome tutorial. Thanks a lot!
Hi,
nice tutorial.
How can i add more domains like: yourdomain.de , mydomain.at etc: ?
Hi Dee,
Have a look at the Postfix documentation:
http://www.postfix.org/VIRTUAL_README.html
Regards,
Mike
Very nice, thanks a lot!
Hello,
sorry, but I spent 4 hours on your guide and did not acheive anything… you promise too much and explain too little. When applying your main.cf for postfix, I will get “fatal error: missing ‘=’ ” or something like that;
And you do not explain the command
adduser –gecos “” –shell /bin/false yourname
at all, what does it do? From where are users authenticated?
I assume someone has basic bash knowledge when administrating a server and setting up an e-mail server. If you follow the tutorial under the same setup, without making any mistakes, you will get what I promised.
Nevertheless you should understand what you are doing.
Use the
manpages of the commands used to understand the options and flags. For exampleman adduserwould have told you what my command does.As of for the main.cf, copy the config again and make sure that it looks exactly the same. Your are missing whitespaces before the options in the ‘helo’ , ‘client’ and ‘data’ restrictions.
Please email me and pastebin config files and log output if you need more help.
That’s answered at the beginning of the tutorial.
hey dude, the “fatal error: missing ‘=’ comes from pasting in the part on
smtpd_recipient_restrictions = reject_non_fqdn_recipient re…. …. ….
with the line breaks intact.
To fix it, pop cursor behind the = and hit delete, then pop in a space between the entries, hit end key, delete, pop in a space… until the last entry…
ie: put em all on one line.
Thats how I cured my same error
Hello,
thank You for nice setup.
I found missing config (not complete) parameters in dovecot.conf for using mail server with squirrelmail client.
I have to fullfill ‘ssl_cert’ and ‘ssl_key’ (end of dovecot.conf file), and now lines look like:
ssl_cert = </etc/ssl/certs/mail.yourdomain.pem
ssl_key = </etc/ssl/private/mail.yourdomain.key
Mail server is ubuntu 14.04
Regards,
Vladimir
Hi Vladimir,
I must have lost that some where because my running setup has what you mentioned in the dovecot config file.
Thank you for seeing that. I just updated the information.
Did you have any problems following this how to on 14.04 because I never tested under 14.04?
Thanks,
Hi Michael,
setup for ubuntu 14.04 passed well. I did not have any problem following Your ‘how-to’.
It seems that 14.04 is same (or very simillar – concerning setup) as 12.04.
Thanks again for usefull mail server setup.
Vladimir
My pleasure. 🙂
I would strongly suggest you change using vim to nano. Vim has quite a learning curve and will probably only serve to confuse the Linux great unwashed while they try to execute the other well presented instruction above.
Hi John,
You can use any text editor you like. It’s just a question of taste. I use “vim” because I like it best. I assume that someone who wants to setup a mail server has already a favourite text editor and will use his choice when working in bash.
Regards
Hi Micheal,
Super great walkthrough, but I’m running into a problem that I don’t know how to fix.
when I do the last command before setting up the email client,
postfix start && service opendkim restartI get the error:
postfix start && service opendkim restart
Do you know why this is?
Thanks so much.
Nevermind, right after posting it I saw where the “&” showed up differently in your code, and I was copying and pasting. All fixed!
Hi Harry,
I’m glad that you figured it out. I’m sorry for the formatting mistake. I saw that the page was showing “&” and I have no idea where that came from. Please let me know should you have any more issues.
Regards,
The shell commands displayed above under ‘Preparing our system’ – ‘Setting up the host name’
seem to have a typo (two ampersands):
echo mail.yourdomain.com && /etc/hostname
Did you mean (greater than character instead of the two ampersands)?:
echo mail.yourdomain.com > /etc/hostname
Regards
andy
Hi Andy,
Thanks for seeing that. I don’t know where that came from…. crazy! I just fixed it.
Thanks and have fun! 🙂
Creating certificates, there is a space on “- out” which should be “-out”
Thank you James. It has been fixed now.
Hi, thanks for the tutorial.
I see you answered this in reply to another comment but main.cf actually does not have any spaces in the relevant sections. You can verify that with the image below, where the left side is your website as displayed to me and the right is the actual HTML source as seen in the dev tools.
http://i.imgur.com/K3rTU4F.png
Mark.
Hi Mark,
Thanks for bringing that to my attention. I fixed that before but my markdown was eating the spaces. 🙁
It should now be displayed correctly.
Regards,
Hi Mark,
It’s a really great tutorial. But what i am thinking is can we use this setup if we don’t have a business class network connection.
Not sure what you are talking about exactly, but you need a server with a static IP and a domain name.
Hi Michael,
Great Tutorial. Could you send me complete document for setting my mail server along with Spamassain/clamav? Also, the mail server should not send/receive spam emails.. your help is appreciated.
Hi Prakash,
Please check this out.
Regards,
Thanks for the guide but I wanted to know, why you set “disable_plaintext_auth = no” in dovecot.conf.
From my understanding I don’t want to send any passwords unencrypted so I set it to true.
Now I got the problem, that my smtp seems to accept mail from unauthenticated users. I ran the test from your mentioned website: https://www.wormly.com/test_smtp_server and i guess the server should reject any mails without password, right?
Thanks for the help
Hi Haxti,
The “plaintext” authentication is tunneled through TLS. Dont worry about that, your password wont be sent in plaintext. disable_plaintext_auth must be set to ‘no’ in this case.
Regards,
Thank you for your answer.
Anytime! 🙂
Firstly, thanks for the great tutorial, your efforts are appreciated.
I came across your page after reading many others and finding it frustrating.
I’m trying to setup a mail server in the same configuration as above, but I want to run a simple SMTP/POP3/IMAP server, just simple plain text password authentication for receiving and sending.
It looks like your configuration only caters for IMAP.
Do you have anything I can refer to in this regard?
Hi Jason,
What is your goal? Why would you want to use POP if you can use IMAP? Look at this.
I don’t see any reason why someone would want to setup a POP email server in 2015.
If you still want to use POP, please read this. Dovecot will no be the best choice.
What do you mean by “simple plain text password authentication”? In my example we are using “plain text password authentication” tunneled through TLS. We don’t want so send our password unencrypted over the net, right? 🙂
I hop this helps a little.
Hi, i did all the steps on a clean server, and i get 10/10 score on mail-tester.com but my mail still goes in the spam folder in Gmail. Makes me pretty sad since it is probably the most used server at the moment. Have you had any experience with this?
Hi Kjetil,
I had the same issue at the beginning. I filled this form and they fixed it within a week.
Note that this depends also on your IP reputation. If you acquired a new IP and someone used it to spam in recent past, it could be that they won’t white list your IP.
It can be a tricky and frustrating thing when dealing with the big providers. I hope they will fix that for you.
Good luck!
Thanks ill see how it goes. Got any other tips for big providers? Have had mixed results with hotmail/outlook.
They are the worst! That’s what I would suggest. Unfortunately there is no magic bullet. They can do what they want because they are big. 🙁
Thanks – This worked like a charm 🙂
I tried this on a virtual machine and behind a router.
I recently changed domain to point to my “external ip” (the ip that you would see). How long does it take for the internet to pick up the change?
I can not connect to my server.
My virtual machine has ip 10.0.2.15 (which is not my external ip and not the ip to point the domain to, right?)
And since I am behind a router:
– do I need port-forwarding? which ports?
– to which device? my vm host device or my virtual machine guest(my router doesn’t seem to detect my virtual machine)?
That’s a bit beyond the scope of this how to. You will need a static IP and NAT with some advanced settings I guess. Why not fire up a vhost for testing? It will cost you almost nothing and it’s very easy and quick. Check here.
Hi,
Thank you very much for the post. I got it sending mails at first try. However I face the following problems and will need you guide.
1. I am unable to receive mails coming from outside (eg. Yahoo, Gmail) though I am able to deliver to them.
2. I am able to send mails using SquirrelMail but not through php mail(). I have been struggling php.ini to get it working but to no avail but once SquirrelMail is able to send, I’m sure I am missing some settings to work with php mail()
3. Mails to Gmail are saved in spam folder instead of inbox. For yahoo, it goes into inbox so no problem.
I need your guide to solve these problems.
Thanks in advance.
Hi,
1. I won’t be able to answer that without seeing the logs. Please check your syslog and show what’s happening when the server gets a new email. Check your ports:
netstat -tulpen|grep LISTEN2. Is this working:
echo testing | mail -s Bla myemail@somewhere.com?3. Make sure to test your mail server and check if all is setup as it should be. Once you are sure that you comply with all rules, read this and fill this form. That can do the trick but it is not always successful.
Dear sir,
Would this also work if I have my website on a shared hosting system here in Belgium but install the mailserversystem on a digital ocean vps droplet in the Netherlands?
http://www.bolleboos.be would then not have the same IP and not even be in the same netrange as mail.bolleboos.be
Also, I would only need to SEND mail, should I setup a complete receiving system then too but with 1 big catchall ?
Kind regards,
Bart
Hi Bart,
Sure thing! You can run the mailserver on a different machine, anywhere in the world. Your DNS records will have to point to the right IP.
Best regards!
Hi Guys,
I followed this guide and after I was able to install both Horde 5 and SquirrelMail, the problem I’m facing on Horde is when I try to send email, i receive a message that the username doesn’t have a domain name, i guess because i login as username but i think I should login as username@mydomain.com, how can I change my authentication to “username@mydomain.com”, I also would like to know how can I troubleshoot logging with outlook, when I try to add to my outlook I cannot login i get this following error, and for last where can I find a way to add more domains to this email server, and if possible different webmails login pages for each domain
Jan 12 02:58:42 mail dovecot: pop3-login: Disconnected (no auth attempts in 0 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
Jan 12 02:58:42 mail dovecot: imap-login: Disconnected: Too many invalid commands (no auth attempts in 0 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
Jan 12 02:58:42 mail dovecot: pop3-login: Disconnected (no auth attempts in 0 secs): user=, rip=x.x.x.x, lip=10.240.0.2, TLS: Disconnected, session=
Jan 12 02:58:43 mail dovecot: pop3-login: Disconnected (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
Jan 12 02:58:43 mail dovecot: pop3-login: Aborted login (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
Jan 12 02:58:43 mail dovecot: imap-login: Disconnected (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, TLS: Disconnected, session=
Jan 12 02:58:43 mail dovecot: imap-login: Disconnected (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, TLS: Disconnected, session=
Jan 12 02:58:43 mail dovecot: pop3-login: Disconnected (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, TLS: Disconnected, session=
Jan 12 02:58:44 mail dovecot: pop3-login: Aborted login (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
Jan 12 02:58:46 mail dovecot: imap-login: Disconnected (no auth attempts in 4 secs): user=, rip=x.x.x.x, lip=10.240.0.2, TLS: Disconnected, session=
Jan 12 02:58:46 mail dovecot: imap-login: Disconnected (no auth attempts in 3 secs): user=, rip=x.x.x.x, lip=10.240.0.2, TLS: Disconnected, session=
Jan 12 02:58:47 mail dovecot: imap-login: Disconnected (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
Jan 12 02:58:47 mail dovecot: imap-login: Disconnected (no auth attempts in 1 secs): user=, rip=x.x.x.x, lip=10.240.0.2, session=
HERE my dovocot.conf
disable_plaintext_auth = no
mail_privileged_group = mail
mail_location = mbox:~/mail:INBOX=/var/mail/%u
userdb {
driver = passwd
}
auth_username_format =”%Ld_%Ln”
passdb {
args = %s
driver = pam
}
protocols = imap imaps pop3 pop3 sieve
protocol imap {
mail_plugins = ” autocreate”
}
plugin {
autocreate = Trash
autocreate2 = Sent
autosubscribe = Trash
autosubscribe2 = Sent
sieve = ~/.dovecot.sieve
sieve_global_path = /var/lib/dovecot/sieve/default.sieve
sieve_dir = ~/sieve
sieve_global_dir = /var/lib/dovecot/sieve/
}
service auth {
unix_listener /var/spool/postfix/private/auth {
group = postfix
mode = 0660
user = postfix
}
}
ssl=required
ssl_cert = </etc/ssl/certs/mail.mydomain.pem
ssl_key = </etc/ssl/private/mail.mydomain.key
# protocol sieve must be enabled
service managesieve-login {
inet_listener sieve {
port = 4190
address = 127.0.0.1
#I only allow connections from localhost
}
service_count = 1
process_min_avail = 1
vsz_limit = 64M
}
service managesieve {
process_limit = 10
}
Hi Junior,
I won’t be able to answer all your questions with the information you provided. Try to test your mailserver first. Start trouble shooting Horde and other stuff when you are sure that all is working like it should. You can use the username for the horde login. Seek help from the Horde community to solve the problem.
I don’t use Windows and therefore I can’t answer anything regarding Outlook. Try it with Thunderbird, if that works, you should seek help from Windows guys.
You can add more domains…look here:
Have a look at the Postfix documentation!
http://www.postfix.org/VIRTUAL_README.html
Best Regards,
Hi there,
thank you very much for your easy-to-understand tutorial. Everything worked out fine for me. I just have one question. Is there any way to change the UNIX password for the users via webmail (roundcube) or other SASL methods? I want to give the users the opportunity to change their password without shell access on my server and without me changing it for them.
Thanks in advance for your answer.
Best Regards,
Luca
Hi Luca,
Thanks for the flowers! I’m happy that everything is working for you. Maybe you want to go with a database instead of Unix accounts, but…. I did not try this, but I had a quick look.
This guy is doing what you are looking for, I think: http://wili.cc/blog/roundcubepw.html
Or look for “roundcube Chpasswd” on your preferred search engine. Its the chpasswd plugin on roundcube.
Best regards!
Hi,
Once more, thank you! Following the link you provided, Roundcube can now change the password.
I have still one more question. Am I right, that postfix and dovecot are configured to only accept encrypted authentications? What about the data transmitted after the auth? Is ist encrypted as well (after the negotiation of a secure connection via STARTTLS)?
Thanks for enlightening my understanding of mail servers and how they work.
Best regards,
Luca
Luca,
If used as in this how to, the connection will be tunnelled thru TLS and therefore be encrypted (check this out). If you only use webmail (who is still using a desktop client anyway?) and the app (ex roundcube) is on the same server, you should allow connection only from localhost. You are using HTTPS, right? There is no more excuse for not using SSL. Look here if you need to set up SSL for free. You can email me if you need anything else.
Best regards,
Hi Michael,
I got some problems with my SMTP 587 port.
I have done all things done step by step but unfortunetly i cant’t get the TLS exeption when I want to send outgoing mail thru the server. What’s the problem? Please let me know how to start the check.
In the past I have done the same tutorial on another server and still working like a sharm, now when I want to to the same I can’t get it work. I only have port 25 for SMTP server.
Thanks a lot.
Gary
Hi Gary,
If you check with netstat and the port is not open, my first guess is that the line below is not uncommented in your /etc/postfix/master.cf.
submission inet n - - - - smtpdBest regards,
Followed your tutorial and it worked perfectly, was easy to follow and understand!
Happy to hear that! Thanks!
I have just maybe naive question, never did it before: where did you get those control panel from? (for setting dns records). Is it your domain host service interface? When I am trying to set domains by my domain hosting place, I can’t put any dot on the end of domainname.com. So how is the next step for me for using mail on ubuntu server 14.04? Greetings
Hi Anna,
Yes, that’s the control panel of the hoster. Please contact the provider to get assistance with the DNS setup, or better, sign up here to spin up a server in minutes. I can only recommend this provider.
Regards!
Excellent tutorial. Everything works perfectly.
Thank you very much!
Thank you Igor. I’m happy that the tutorial was useful for you!
Installing
apt-get install postfix postfix-policyd-spf-perl postgrey dovecot-core dovecot-imapd opendkim opendkim-tools && postfix stop
Choose Internet Site and press ‘ok’ 2 times when asked by the postfix installer.
====
needs to add one thing… before you choose internet site it asks if you wnat to creat ssl… you have to say no…
Thanks for the comment. I’ve updated as you suggested.
Hey Michael,
i had to reinstall my whole server, so smtp too.
I’ve got a problem:
– google sais the mails i send to them seem unencrypted
Some of my ports seem wrong:
tcp6 0 0 :::25 :::* LISTEN 0 15183 1704/master
tcp6 0 0 :::993 :::* LISTEN 0 128436 15343/dovecot
tcp6 0 0 :::587 :::* LISTEN 0 77009 1704/master
tcp6 0 0 :::143 :::* LISTEN 0 128434 15343/dovecot
I checked every file you’ve mentioned in your tutorial twice, i don’t know what’s wrong.
Regards,
Dee
Hi Dee,
Good point! After looking over the tutorial, I found out that I missed one line in main.cf (now fixed).
smtp_tls_security_level=may was missing which will enable TLS for outgoing mails if supported by the receiving server.
You should have these 2 lines in main.cf:
smtpd_tls_security_level=maysmtp_tls_security_level=may
Best regards,
If you want to edit multiple Domains and sign each of them with DKIM use this post:
http://askubuntu.com/a/441536/404038
You are the man thank you so much !
Everything works correctly . You saved my life 🙂
🙂
Hie,
i have created my own mail server using this tutorial but when i mail through my mail server,all my mails are going into spam.. Can u tell me what can i do nw to send mail on inbox..
Hi Swati,
That can be a big problem. Big providers do what they want and sometimes if your IP has no (or bad) reputation, they will deliver to Spam.
I had the same issue with hotmail and gmail.
Please follow the steps here and hopefully that will help, but there is no guarantee.
Best regards,
nice article and very helpful.
I can confirm that this tutorial also works on Ubuntu 16.04.2 x64. I spun up an instance(DO) 16hours ago. I’ve sent emails to gmail, they were marked spam but I manually unmarked them as spam. Now I can send to gmail unchallenged and immediately.
I have also tested multiple sends to outlook(office 365 account), receiving is actually not a problem, sending from that account was delayed for a few minutes. But after I received that first email from outlook->my instance, its been immediate without challenges.
I have two instances at digitalocean. One is running mail-in-a-box setup, which was automagically setup. The other is running this tutorial, which was a manual setup. After 16hrs, sending back and forth between the two instances is also good. No issues.
Now I gotta figure out how to integrate ClamAv with SpamAssassin.
This tutorial is magic, it gets it done. Thanks Michael!
Thanks so much for the feedback and additional information!
I use SpamAssassin with this configuration, so let me know if you have any questions.
Hello,
I am here because other tutorials on installing debian, postifx, and dovecot neglect security. Michael seems to have built it in, so I’m going to try it. I have to have horde on top, so I’m glad others have done it — although, apparently, with some problems. I’m planning to import mail from an old server into this one after it’s built, and I’m hoping the reputation problems will be easier to overcome with this system than with those I used previously. I’ll report on my results. Thank you, Michael, for what appears to be a genuine effort to help.
Love the tutorial… Can it work in Ubuntu 16.04 LTS?
Thanks in advance!
Hi Josh,
Yes it will work on 16.04 too.
Regards,
Hi, I get after apt-get install postfix postfix-policyd-spf-perl postgrey dovecot-core dovecot-imapd opendkim opendkim-tools && postfix stop and selection of Internet site following lines:
>postfix: error: to submit mail, use the Postfix sendmail command
>postfix: fatal: the postfix command is reserved for the superuser
I’m on ubuntu 17.10. Any ideas whats wrong?
Best
Mici
Hi,
Did you use
sudo? If so, please do the same thing but become root before running the command.Let’s see if you are getting the same error…
Rgs,
Hi,
Great step by step training by the way to configure your own web server. I got it working to my thunderbird mail client but having a problem connecting it to the outlook mail client. Getting the following error:
Jul 28 14:31:06 localhost postfix/submission/smtpd[9956]: connect from unknown[49.147.52.113]
Jul 28 14:31:07 localhost postfix/submission/smtpd[9956]: NOQUEUE: reject: RCPT from unknown[49.147.52.113]: 504 5.5.2 : Helo command rejected: need fully-qualified hostname; from= to= proto=ESMTP helo=
Jul 28 14:31:07 localhost postfix/submission/smtpd[9956]: lost connection after RCPT from unknown[49.147.52.113]
Maybe you can help me?
Hi,
I’m sorry for the late response…I was away for a while.
Did you resolve the issue?
If not, try to remove the 2 entries below from your main.cf and let me know if that worked.
reject_non_fqdn_helo_hostname
reject_invalid_helo_hostname
Rgs
The checking tool at appmaildev.com is not present on their website. I have found a new one at https://www.emailtooler.com/authentication-validator/ that is working the same. Thank you for the instructions!
This tutorial finally helped me to set up a working mailserver. Thanks so much!
I have added some users with the command ‘adduser –gecos ” –shell /bin/false yourname’.
However this command did not aut-created a maildirectory within the user directory.
How to accomplish this?
This should help…
https://wiki.dovecot.org/MailLocation
Mailbox autocreation
Dovecot in the 1.x era created mailboxes automatically regardless of whether mail_location was set. In 2.x autocreation only gets triggered if mail_location is correctly set. You’ll see something like this if you enable debug logging:
Debug: Namespace : /home/user/Mail doesn't exist yet, using default permissionsDebug: Namespace : Using permissions from /home/user/Mail: mode=0700 gid=default
and a Mail/.imap directory will be present once that process has concluded. This is the easiest way to ensure a freshly created user is correctly set up for access via Dovecot.